1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
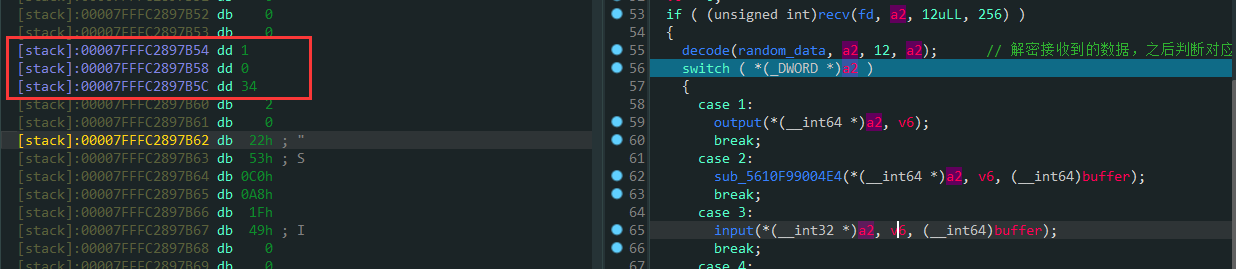
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
| #include<iostream>
#include<Windows.h>
#include<string>
#include <iomanip>
using namespace std;
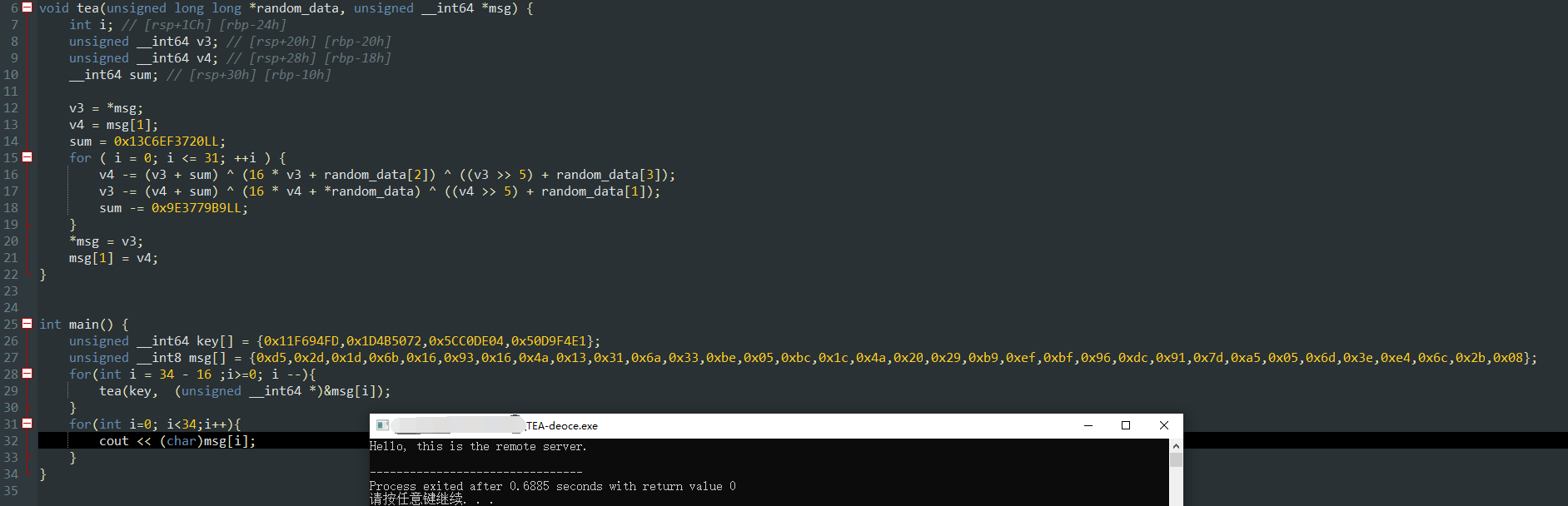
void tea(unsigned __int64* key, unsigned __int64* msg) {
int i;
unsigned __int64 v3;
unsigned __int64 v4;
__int64 sum;
v3 = msg[0];
v4 = msg[1];
sum = 0x13C6EF3720LL;
for (i = 0; i <= 31; ++i) {
v4 -= (v3 + sum) ^ (16 * v3 + key[2]) ^ ((v3 >> 5) + key[3]);
v3 -= (v4 + sum) ^ (16 * v4 + *key) ^ ((v4 >> 5) + key[1]);
sum -= 0x9E3779B9LL;
}
*msg = v3;
msg[1] = v4;
}
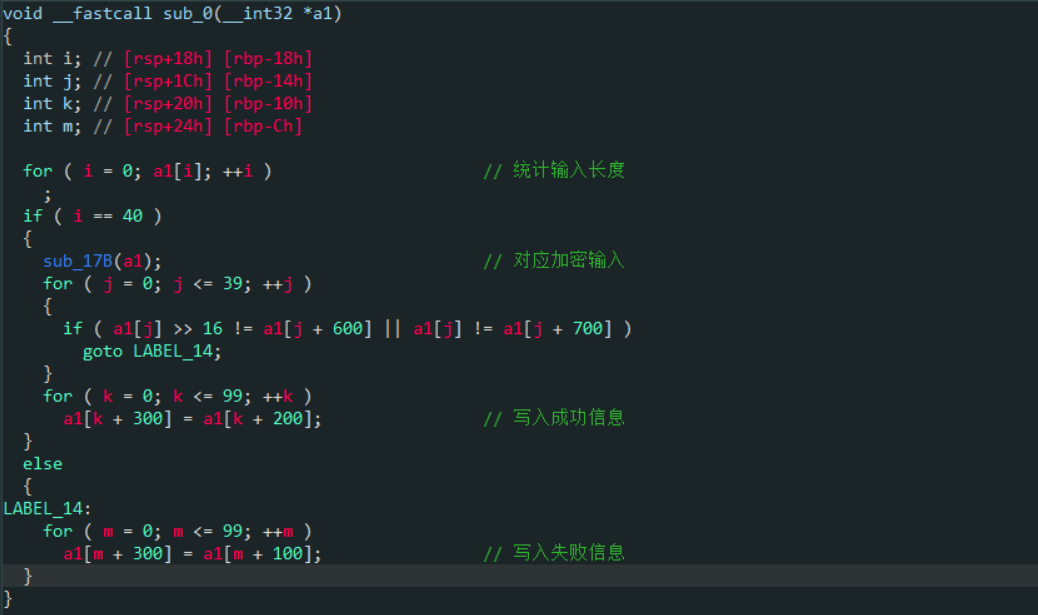
unsigned __int32 decryptInstruction(unsigned __int8* instruction) {
unsigned __int8 key[] = { 0xfd,0x94,0xf6,0x11,0x00,0x00,0x00,0x00,0x72,0x50,0x4b,0x1d,0x00,0x00,0x00,0x00,
0x04,0xde,0xc0,0x5c,0x00,0x00,0x00,0x00,0xe1,0xf4,0xd9,0x50,0x00,0x00,0x00,0x00,
0x17,0xcb,0x56,0xc1,0x7a,0x19,0xfb,0x2d,0xfe,0xdb,0x84,0x72,0x97,0x28,0xc8,0x94
};
for (int i = 0; i < 12; i++) {
instruction[i] ^= key[i + 32];
}
unsigned __int32 a = *(unsigned __int32*)&(instruction[0]);
unsigned __int32 b = *(unsigned __int32*)&(instruction[4]);
unsigned __int32 c = *(unsigned __int32*)&(instruction[8]);
cout << endl;
string result = "[" + to_string(a) + "," + to_string(b) + "," + to_string(c) + "]";
cout << result << endl;
return c;
}
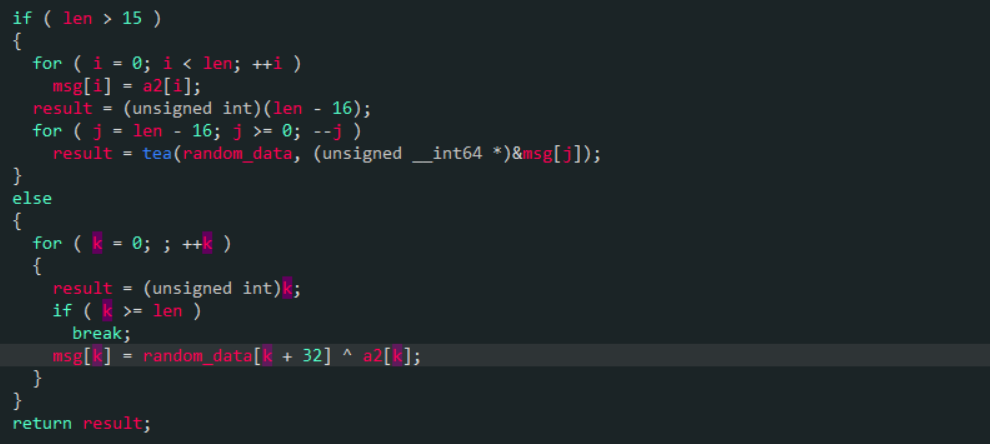
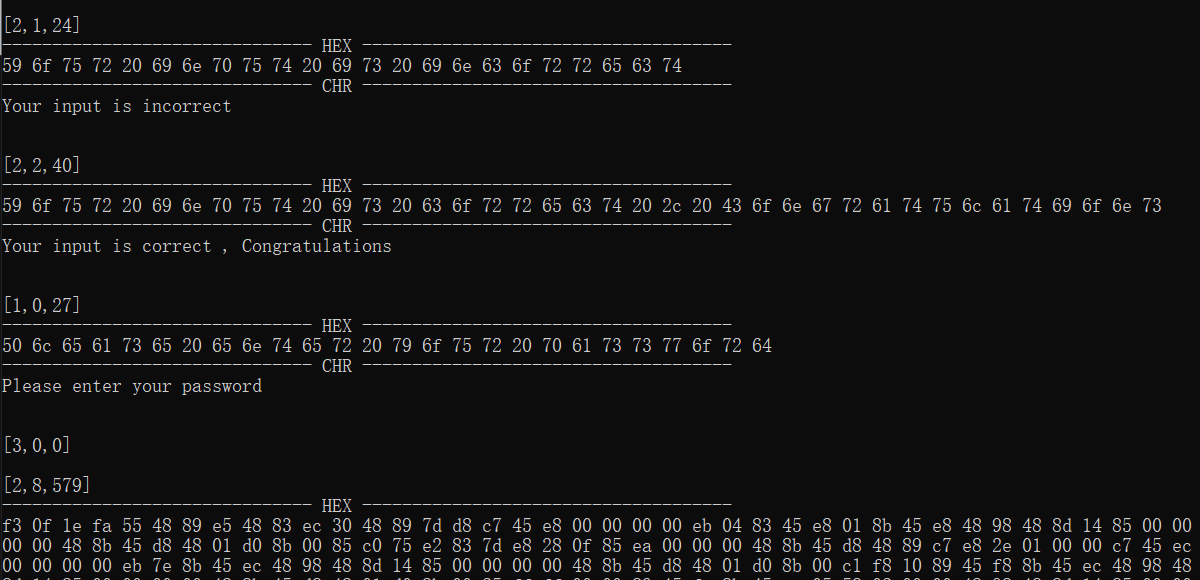
unsigned __int32 decryptData(unsigned __int8* msg, unsigned __int32 pos) {
unsigned __int32 len = 0;
if (msg[pos + 1] == 0xcb && msg[pos + 2] == 0x56 && msg[pos + 3] == 0xc1) {
len = decryptInstruction(&msg[pos]);
pos += 12;
}
if (len) {
unsigned __int64 key64[] = { 0x11F694FD,0x1D4B5072,0x5CC0DE04,0x50D9F4E1 };
for (int i = len - 16; i >= 0; i--) {
tea(key64, (unsigned __int64*)&msg[i + pos]);
}
int flag = 1;
cout << "------------------------------- HEX -------------------------------------" << endl;
for (int i = 0; i < len-1; i++) {
cout << setw(2) << setfill('0') << hex << (int)msg[pos + i] << " ";
if (msg[pos + i] < 32 || msg[pos + i] > 127 ) {
flag = 0;
}
}
cout << endl;
cout << "------------------------------- CHR -------------------------------------" << endl;
if (flag) {
for (int i = 0; i < len; i++) {
cout << (char)msg[pos + i];
}
}
cout << endl;
pos += len;
}
return pos;
}
int main() {
unsigned __int8 msg[] = { 0x15,0xcb,0x56,0xc1,0x7b,0x19,0xfb,0x2d,0xe6,0xdb,0x84,0x72,0x11,0xfd,0x38,0x2b,0xc3,0xeb,0x73,0x90,0x37,0xf7,0xdf,0xa4,0xb0,0xca,0x55,0x3f,0x4d,0xc6,0x7f,0x81,0xb7,0x1b,0x7f,0x92,0x15,0xcb,0x56,0xc1,0x78,0x19,0xfb,0x2d,0xd6,0xdb,0x84,0x72,0x7c,0x85,0x26,0xcc,0x3d,0x63,0x83,0xbb,0xcf,0x01,0x59,0x59,0x06,0x48,0x58,0x6e,0x7d,0xd0,0x8b,0x49,0xcc,0x1e,0xe7,0xf5,0x19,0xec,0x20,0x65,0x92,0x25,0x48,0x42,0xb7,0xf3,0x3d,0x25,0x64,0x66,0x40,0xab,0x16,0xcb,0x56,0xc1,0x7a,0x19,0xfb,0x2d,0xe5,0xdb,0x84,0x72,0xc0,0x08,0xba,0x6c,0x15,0x33,0x4f,0x76,0x48,0x5d,0x8c,0x17,0x08,0x2f,0x44,0x68,0xad,0xdb,0xb3,0xa6,0x2d,0x20,0xe7,0x54,0x10,0x5d,0x10,0x14,0xcb,0x56,0xc1,0x7a,0x19,0xfb,0x2d,0xfe,0xdb,0x84,0x72,0x15,0xcb,0x56,0xc1,0x72,0x19,0xfb,0x2d,0xbd,0xd9,0x84,0x72,0x34,0x19,0xb3,0xea,0x63,0x30,0x6f,0xf1,0x22,0x41,0x73,0xd8,0x34,0xb1,0xf9,0xc4,0x36,0x33,0x2f,0x39,0xec,0x2a,0xa1,0x02,0xbb,0x77,0x47,0x85,0x9d,0x50,0x79,0x36,0x74,0xb0,0x5a,0x56,0xf1,0x4e,0xe2,0x94,0x91,0x89,0x59,0x44,0xcb,0xf1,0xf6,0x84,0x6a,0x98,0x31,0xf8,0xdd,0x56,0x66,0x20,0x2c,0x4b,0x0d,0x55,0x8a,0x69,0x02,0x39,0xb1,0xde,0xce,0x43,0x22,0xfe,0x53,0x5c,0x07,0x42,0xcc,0x2f,0x37,0x37,0x85,0x77,0xb9,0x99,0xea,0xab,0x71,0x3d,0x85,0x36,0x43,0xbc,0x37,0x9d,0xac,0x7f,0x7f,0x47,0x1e,0xf2,0x24,0x0b,0x88,0x98,0xfa,0xc4,0x43,0x11,0x49,0xaa,0x27,0xa6,0x55,0x07,0xdb,0x39,0xa9,0x11,0x1d,0xea,0x80,0x2a,0x80,0x35,0x06,0xfb,0xd4,0xa2,0xd5,0x58,0x06,0x89,0x74,0xf9,0x93,0xdc,0xab,0x45,0x87,0xa5,0x62,0x0d,0xb6,0x90,0x9a,0x95,0x1d,0xcf,0x8b,0xb6,0x5d,0x4f,0x8e,0x92,0xac,0x83,0x00,0xfd,0x04,0x9b,0xb3,0x21,0x81,0x99,0x70,0x5b,0xab,0xb2,0x55,0xe7,0xda,0xef,0x40,0xa2,0x8c,0x1d,0x7e,0x3f,0x74,0xcb,0x1d,0x44,0x68,0x7b,0xe1,0x27,0x25,0x8a,0xaf,0xc4,0xdb,0xda,0xf0,0x92,0x66,0xda,0xa6,0x86,0x05,0xe2,0x50,0xaa,0x24,0x4c,0x17,0x9d,0x75,0x9d,0x22,0xe9,0x0e,0xd3,0xd8,0xa9,0xbf,0x15,0x5f,0xae,0x86,0xc7,0x21,0xed,0x8e,0xe5,0x60,0x3c,0x46,0x13,0xac,0x47,0xe5,0xa8,0x00,0x79,0xb9,0x09,0x72,0x72,0x77,0xff,0xf3,0x1d,0x20,0x52,0x9b,0x3c,0x02,0x2e,0x3b,0x1a,0x36,0x16,0xd6,0x39,0xca,0x03,0x65,0x86,0xef,0x17,0xd3,0xdc,0x9b,0xdf,0x1e,0xee,0xc5,0x85,0x9f,0x00,0x22,0x51,0x4f,0x29,0xb2,0x40,0xf3,0x0c,0x81,0x8e,0x7f,0xdd,0x47,0x8f,0x36,0x77,0x99,0x78,0xc0,0x88,0x85,0xb2,0x26,0x6e,0x3c,0xf5,0x99,0xd0,0xa4,0xc2,0x7b,0xca,0x46,0x15,0x72,0x0a,0x08,0xe1,0x39,0x16,0xec,0x4a,0x6e,0xf5,0xc9,0x43,0xdd,0xb2,0x55,0x66,0xe6,0x20,0x72,0x6f,0x56,0xc5,0x16,0x09,0x13,0x56,0x4d,0x68,0x3b,0xad,0xcc,0x72,0x04,0xec,0x8e,0x70,0x80,0x22,0x1d,0xe3,0x25,0xa4,0x31,0xa0,0x68,0x0e,0x9e,0x10,0x8e,0x42,0x7c,0x7b,0xc3,0x80,0x7b,0x86,0xc7,0x88,0x20,0xbc,0x9c,0x23,0x40,0x70,0x9d,0xa3,0x52,0xd9,0x53,0xae,0xa8,0x05,0xa0,0x4b,0x53,0xf2,0xd8,0x8f,0x7b,0x8f,0xae,0x50,0xe5,0xba,0x2d,0xe5,0x56,0x15,0xbc,0x9b,0x2e,0x52,0x61,0x67,0x22,0x6e,0x75,0xf5,0xc8,0x82,0x75,0x93,0x28,0x1f,0x23,0xa6,0x5e,0x50,0x98,0xe0,0xe8,0xe2,0x62,0x3e,0xe4,0xf8,0x92,0xba,0xc7,0x6e,0x69,0x87,0xa0,0x58,0x32,0xbc,0x0b,0x84,0x21,0x5b,0xb7,0x4e,0xd8,0x37,0x86,0xbd,0x55,0x26,0x5e,0x61,0xba,0x57,0x02,0x17,0x0f,0xda,0x63,0xe0,0x1a,0x44,0xd6,0xb8,0xa6,0xf1,0x74,0x0a,0x6c,0x03,0x80,0x30,0x95,0xe5,0x17,0x6b,0xde,0x18,0xee,0x87,0x3d,0xcd,0x63,0x80,0xde,0x9f,0x32,0x5f,0x1c,0x43,0x6c,0x11,0xe3,0x25,0x0c,0xeb,0xce,0xce,0xb3,0x19,0xa4,0x9a,0x4e,0x3f,0x2f,0x62,0xcf,0xd1,0x37,0xb6,0x02,0xe2,0x7f,0x39,0x74,0xa1,0x13,0xdf,0x41,0x42,0x87,0xda,0x48,0xaf,0xd9,0xe8,0xc7,0xef,0x0b,0xdb,0x4d,0x34,0x53,0x13,0xb5,0x2d,0x66,0x22,0x02,0xf5,0x43,0xf4,0x26,0xf8,0x27,0x14,0x32,0xa2,0x01,0x86,0xb1,0xdc,0x7f,0x70,0xd4,0x12,0x3d,0xef,0x1c,0x37,0x45,0xc1,0xff,0xe7,0xf4,0x01,0x7f,0xf6,0x0e,0x0b,0x74,0x86,0xf0,0xe8,0xdb,0x90,0x88,0x9a,0x36,0x07,0x25,0x83,0xdd,0xb2,0x6d,0xbd,0x37,0x77,0x81,0x15,0xcb,0x56,0xc1,0x7e,0x19,0xfb,0x2d,0x5e,0xdb,0x84,0x72,0x63,0x42,0x4f,0xb4,0x92,0x1f,0x22,0x4e,0xb2,0xd4,0x45,0x18,0x3f,0x9b,0xc6,0x54,0x1d,0x1a,0xc7,0x70,0x72,0xa6,0xe6,0x16,0xe6,0x82,0x6c,0xbb,0xeb,0xe9,0x6a,0xf2,0x29,0xe7,0x96,0x20,0x46,0x28,0x69,0xe5,0x16,0x86,0xd4,0xd5,0x23,0xf7,0x82,0xb2,0xe5,0xb4,0x3a,0x76,0x94,0x03,0xbf,0x62,0xf1,0xb8,0x75,0x12,0x01,0x3f,0x95,0xd0,0x68,0xdc,0x04,0xbe,0xb3,0x37,0xf8,0x74,0x1b,0x47,0x13,0x86,0xa7,0x74,0x6e,0xbc,0x7b,0x9c,0x7a,0x95,0x68,0xed,0x9b,0x59,0x09,0x36,0xcd,0xc5,0x33,0xf6,0xf9,0x43,0xe3,0xa3,0x79,0x66,0x36,0x2b,0x62,0x09,0x2c,0xe5,0xa3,0xc5,0x3a,0x95,0xb3,0x3d,0x0f,0xf1,0xac,0x2c,0x58,0x00,0xb6,0x7b,0x8c,0xc4,0x0d,0x61,0x4b,0x8d,0xf7,0x4d,0x41,0x14,0xd4,0xbb,0x71,0x04,0xb5,0x45,0xac,0x7d,0x0b,0x9e,0xb6,0x06,0x57,0x8f,0xd6,0x35,0x61,0x57,0x87,0x40,0xce,0x7e,0xea,0xa1,0x89,0xba,0xac,0xd4,0x36,0xae,0x15,0xcb,0x56,0xc1,0x7f,0x19,0xfb,0x2d,0x5e,0xdb,0x84,0x72,0xec,0xc4,0x94,0x2b,0xbc,0x4e,0x2b,0xbe,0xc5,0xc4,0xad,0xb7,0x91,0xa7,0x09,0x62,0x98,0xf6,0x34,0x7c,0x4a,0x27,0x73,0x64,0xce,0xa8,0x94,0x23,0x4b,0xdc,0xf6,0x98,0x11,0xf3,0x1c,0xe6,0x44,0xba,0xe1,0x0e,0xdc,0x0d,0xe4,0xcc,0xc2,0x00,0xa4,0x4f,0xa0,0xe2,0xfa,0xa4,0xd2,0xeb,0x3b,0x28,0xdc,0xec,0xc3,0xa4,0x68,0xef,0xdb,0xfa,0x7d,0xe2,0x72,0x8b,0x27,0xdf,0xaf,0xd1,0xa5,0xdf,0x48,0x03,0xa7,0x98,0x6c,0xfa,0x76,0x8f,0xb1,0xf9,0x75,0x1b,0xa1,0xa7,0xd4,0x7c,0x9a,0x69,0x28,0x97,0x88,0x10,0xd7,0x6d,0xce,0xb8,0x19,0x73,0x8f,0x46,0x84,0x63,0x7d,0x3d,0xdd,0x2c,0xc4,0x1e,0x2a,0x45,0x85,0xa3,0x66,0xd4,0xa4,0x6b,0x32,0xdb,0x59,0x50,0x8f,0x34,0xbf,0x5c,0x65,0x4b,0xe7,0xb5,0xc8,0x6e,0x24,0xcc,0xa5,0xd1,0x01,0x37,0x38,0xc3,0x2b,0xa9,0xb6,0x08,0x3e,0x76,0xe0,0xf9,0x3c,0x80,0xfe,0x71,0x22,0x61,0x84,0x1e,0x54,0x63,0x15,0xcb,0x56,0xc1,0x7c,0x19,0xfb,0x2d,0x5e,0xdb,0x84,0x72,0x60,0xfd,0x33,0x8f,0xdc,0xec,0xb0,0x96,0xe2,0x6a,0x56,0x60,0x30,0x82,0xa5,0x8f,0x5b,0x1f,0xb0,0xff,0xb7,0xfc,0x8f,0xaa,0xc3,0x35,0x89,0xec,0x52,0xed,0x02,0x25,0x6a,0xba,0x88,0xb2,0xc2,0x83,0x64,0x33,0xa5,0xd1,0x46,0xc6,0xef,0xe7,0x84,0xd4,0x7d,0xa7,0xa7,0xff,0xc4,0x25,0x6f,0x3d,0xce,0x73,0x31,0x4c,0x01,0x71,0xf8,0x9e,0x9a,0x4f,0x6a,0x95,0xf5,0x9e,0x84,0x60,0xd2,0xb6,0x5f,0xe1,0x78,0xda,0xba,0x5f,0xaf,0x8d,0x34,0xd9,0x9e,0x32,0xa5,0x0a,0xef,0xbb,0xb7,0xed,0x9c,0x95,0x07,0x76,0x59,0x58,0x87,0x0d,0xd2,0xe1,0x83,0x6f,0xe6,0x08,0x21,0x5c,0xa7,0x53,0xa7,0x12,0x5f,0x3c,0xb8,0x6a,0xc3,0x2d,0x11,0x49,0xcf,0x2a,0x14,0x4b,0x87,0x3f,0xc7,0xa9,0x69,0x14,0xd3,0x76,0xed,0x2f,0xe8,0x8d,0x36,0xa6,0x09,0x59,0x6a,0x68,0xd8,0xbb,0x76,0xe7,0x1d,0x1b,0x81,0xa8,0xdb,0x36,0x18,0x27,0x1f,0x00,0x2f,0xf6,0xfb,0x58,0x15,0xcb,0x56,0xc1,0x7d,0x19,0xfb,0x2d,0x5e,0xdb,0x84,0x72,0xb7,0x2d,0x65,0x7a,0xbc,0x1a,0x3c,0x21,0x33,0xfa,0x45,0xfd,0x83,0x4d,0x28,0xfc,0xe3,0xb5,0xbd,0xd8,0xf1,0x11,0xbf,0xa6,0x13,0x86,0xa3,0x06,0xaa,0x74,0x59,0x8e,0xa6,0xe5,0x02,0x2f,0x4a,0xac,0x8d,0x9a,0xcd,0x44,0x2c,0x44,0x46,0x5e,0xb3,0x34,0xc2,0x6d,0x06,0x0d,0xfc,0x8f,0x4f,0x59,0xc1,0x3f,0x32,0x25,0xa5,0xea,0x11,0x1f,0x9e,0x3e,0x9e,0xf4,0xc7,0x5f,0x40,0xb8,0x5c,0x43,0xdb,0xdd,0x5d,0x30,0x97,0x0c,0xde,0x50,0x7c,0xd9,0x6f,0xa6,0xa8,0x89,0x70,0xe2,0x3c,0x1d,0xc1,0xcb,0x9a,0x1e,0xab,0x2f,0x4c,0xc1,0x64,0x44,0x22,0x6a,0xff,0x6c,0x49,0xdd,0x13,0xe0,0x30,0x24,0x0e,0xa3,0x22,0x67,0xa1,0x69,0x9b,0x5b,0x8c,0x83,0xd0,0x5c,0x1c,0xc2,0x57,0xf5,0x02,0x8d,0x64,0x9e,0x2b,0x58,0xd9,0x6a,0x1f,0x59,0xfc,0xd4,0x2f,0x02,0x71,0x79,0xe7,0x40,0x0f,0x2c,0x64,0xc3,0x06,0x3a,0xe1,0xf9,0xc4,0x96,0xec,0x01,0x9e,0xba,0x12,0xcb,0x56,0xc1,0x72,0x19,0xfa,0x2d };
unsigned __int32 pos = 0;
while (pos != sizeof(msg)) {
pos = decryptData(msg, pos);
}
}
|