Angr 学习笔记
安装
安装的话angr支持了Python 3.x可以不用去折腾2.x的版本了,对于Windows似乎可以直接:
就可以完成大部分需要库的安装,对于Linux可能会有一些复杂,这里给出一个链接给大家参考一下:
https://www.cnblogs.com/lxy8584099/p/13668749.html
本人是在Windows下安装的,也没遇到网上出现的缺失文件的现象。出现问题了我也不清楚呀 :(
部分使用教程
导入 angr 包
似乎这一部没有出差错就是说明安装成功了。
新建一个 angr 工程
1 2 "<需要拿来解题的文件>" )
上述过程相当于完成了angr的加载。
初始化 angr
Unicorn是 angr的依赖库,在Unicorn下可以执行任意一段二进制的代码,我们对此需要告诉其从哪里开始,因此我们需要对angr进行初始化
1 2
执行 angr
初始化后我们需要执行angr
1 2
上述过程中我们设置了一个模拟器,接下来我们需要告诉程序应该到哪里去,我们需要设置目标地址:
1 sm.explore(find = "<目标地址>" )
此时如果我们找到了通向对应的目标地址的时候,将其打印出来其符号向量:
1 2 3 4 5 6 7 if simulation.found:0 ]print (solution_state.posix.dumps(sys.stdin.fileno()))else :raise Exception('Could not find solution' )
00_angr_find
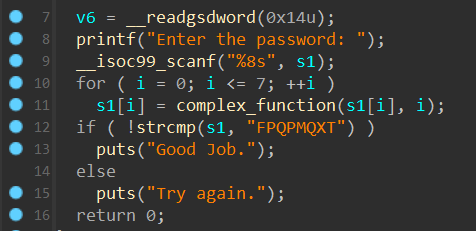
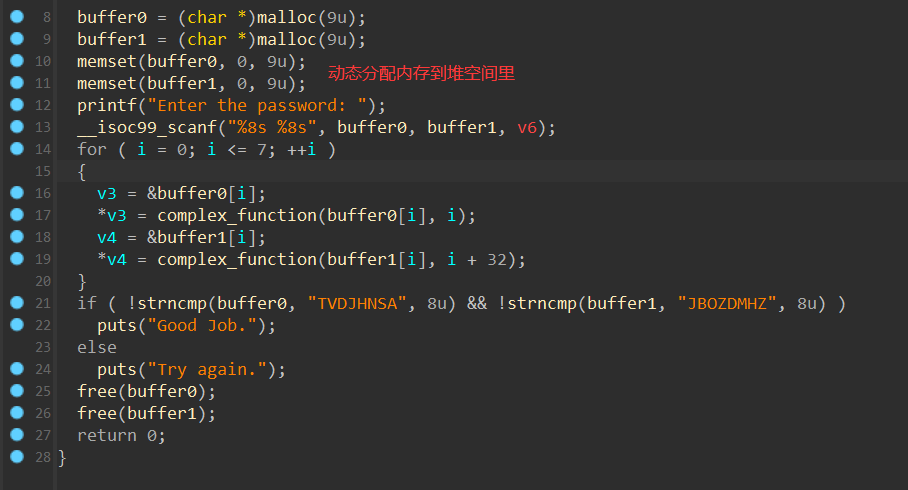
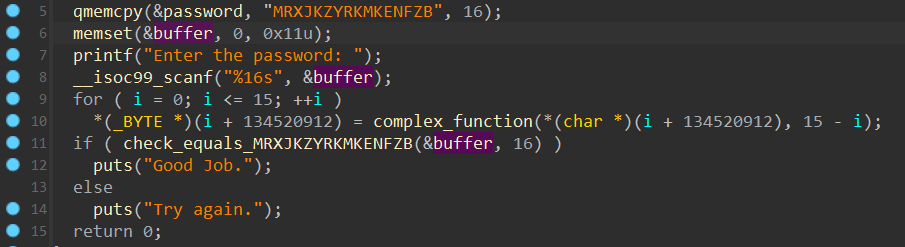
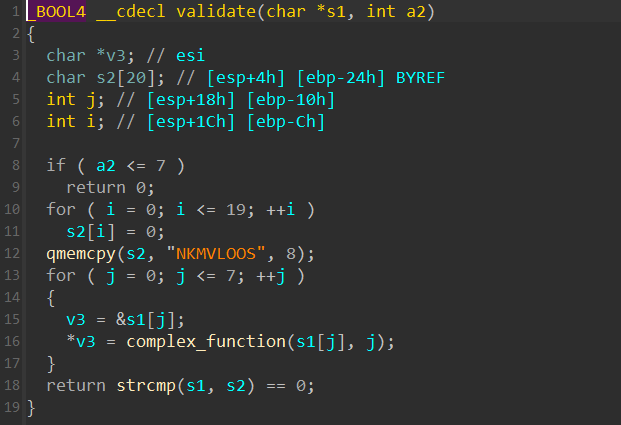
第一题拖进IDA分析可以看到是十分简单的,其关键部分便是中间的那个complex_function,我们尝试用angr来进行解题 ( 虽然爆破也可以直接执行 )。
我们找到对应目标 ( Good Job ) 的地址,将其导入进行求解
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 import sysimport angrdef main (argv ):'../program/00_angr_find' 0x0804867D if simulation.found:0 ]print (solution_state.posix.dumps(sys.stdin.fileno()))else :raise Exception('Could not find solution' )if __name__ == '__main__' :
值得注意的是在输出语句中print(solution_state.posix.dumps(sys.stdin.fileno())),其中的dumps在Python 3.x下运行成功,但是在文档中看到有些写的是dump,不清楚其是否为Python 2.x运行的,上述脚本运行不成功时可以试试看各改一下输出的dump
通过上述脚本我们可以直接得到目标地址的值在解密后得到的目标答案。
本题中我们了解到了如何编写angr脚本,了解了如何创建项目,创建模拟器以及如何约束模拟器到对应的地址处和输出约束求解的结果。
1 2 3 4 5 angr.Project(file_path) 0 ]print (solution_state.posix.dumps(sys.stdin.fileno()))
01_angr_avoid
将程序拖进IDA,反编译主函数程序显示函数过大,无法反编译,在这个题目中我们主要学习angr的avoid的使用,对此我们利用avoid来去除我们不想要到达的地址。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 import sysimport angrdef main (argv ):'../program/00_angr_find' 0x080485E0 0x080485F2 if simulation.found:0 ]print (solution_state.posix.dumps(sys.stdin.fileno()))else :raise Exception('Could not find solution' )if __name__ == '__main__' :
需要注意的是对应的good的地址不是这个字符串的地址,而是打印字符串时的汇编代码对应的地址。
通过上述例子,我们学会了如何加入规避的地址来进行进一步的约束求解
1 2 3 print_good_addr = XXXX
01_angr_condition
将程序拖入IDA可以看到主函数还是和上一题一样,函数过大而无法反编译,同时我们观察一下主函数里的数据可以看到有多个Good Job和多个Try again,此时的一个单一的约束并不能很好的起作用,此时用到了angr中的condition来对多个结果进行约束求解。
1 simulation.explore(find=print_good_addr, avoid=try_again_addr)
之前我们的约束条件都是上面的explore中加入find和avoid的函数地址,但是实际上find和avoid对应的参数可以是一个函数,我们将在这个函数里面进行一个条件的约束
1 2 3 4 5 6 7 def good_job (state ):return 'Good Job' in str (stdout_output)def try_again (state ):return 'Try again' in str (stdout_output)
stdout_output = state.posix.dumps(sys.stdout.fileno())用来获取标准输出的字符
我们利用获取的标准输出字符来进行创建函数,而进一步对我们的条件进行约束求解,那么我们传入的便不再是一个单一的地址,可以对输出的字符集合进行集体约束求解,得到我们想要的结果。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 import sysimport angrdef good_job (state ):return 'Good Job' in str (stdout_output)def try_again (state ):return 'Try again' in str (stdout_output)def main (argv ):'./02_angr_find_condition' if simulation.found:0 ]print (solution_state.posix.dumps(sys.stdin.fileno()))else :raise Exception('Could not find solution' )if __name__ == '__main__' :
上述例子,我们学会了对输出条件来进行集体约束求解,明白了simulation.explore对应的参数值可以是一个函数,在函数中我们调用标准的输出库,来对输出字符进行约束求解。
1 2 3 4 5 6 def good_job (state ):return b"XXX" in solution_state.posix.dumps(0 ) def try_again (state ):return b"XXX" in solution_state.posix.dumps(0 )
03_angr_symbolic_registers
打开题目一看,程序要求我们输入的是 3 个数据,通过三个复杂的函数进行运算,当三个数运算处理后的返回值均为 1 时,判断输入正确,反之判断错误。之前有一个学长去问过angr_CTF库的原作者问多个输入angr可以直接处理吗,原作者回答可以直接处理,但是为了学习目的我们不直接按照之前几个题目的方式来约束地址或者输出来进行运算。
我们还是给出之前的代码写法:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 import sysimport angrdef good_job (state ):return 'Good Job' in str (stdout_output)def try_again (state ):return 'Try again' in str (stdout_output)def main (argv ):'./03_angr_symbolic_registers' if simulation.found:0 ]print (solution_state.posix.dumps(sys.stdin.fileno()))else :raise Exception('Could not find solution' )if __name__ == '__main__' :
在题目名称中我们可以看到符号化寄存器的英文,那么什么是符号化寄存器?
设置状态的寄存器值,符号化寄存器值含义就是将寄存器内存储的值设为自变量,而后类别列方程加入约束条件内
似乎有点类似于z3设置多个未知数然后带入方程组进行约束求解。那么我们要怎么做呢?我们先观察一下程序的输入:
可以看出来我们的 3 个输入数据先后从ecx中转移到了eax、ebx、edx里,同时在后续复杂函数的处理部分中没有改变 3 个寄存器来进行其他处理,对此我们可以直接设置 3 个未知数来代替这三个寄存器,来参与下面函数的运算和执行。
要将寄存器符号化我们需要引入一个新的函数库:import claripy,由于我们不再是从主函数( main )直接执行我们的符号化向量,我们需要重新设置一个起始地址:
1 2 3
其中的project.factory.blank_state与之前的project.factory.entry_state不同了,blank_state相当于表示一个空的地址,需要我们把开始地址进行导入。
接下来便是将寄存器进行符号化,我们便利用到了之前引入的claripy库,下面给出示例:
1 2 3 4 5 6 7 '<符号向量取名>' , bit_length)
那么我们想要输出对应找到后的寄存器值又该怎么处理呢?
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 if simulation.found:0 ]eval (register)'%x' % (solution)print (solution)else :raise Exception('Could not find the solution' )if simulation.found:0 ]eval (register1)eval (register2)'%x %x' % (solution1,solution2)print (solution)else :raise Exception('Could not find the solution' )
此时新的脚本可以如下编写:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 import sysimport angrimport claripydef main ():'../program/03_angr_symbolic_registers' 0x0804890E 32 'psd0' , bit_length)'psd1' , bit_length)'psd2' , bit_length)def good_job (state ):return b'Good Job.' in stdout_contentdef fail (state ):return b'Try again.' in stdout_contentif simulation.found:0 ]eval (psd0)eval (psd1)eval (psd2)'%x %x %x' % (solution0, solution1, solution2)print (solution)else :raise Exception('Could not find the solution' )if __name__ == '__main__' :
上述过程中我们学习了符号化寄存器,修改对应的输出格式,同时如何更改执行的起始地址:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 '<符号向量取名>' , bit_length)if simulation.found:0 ]eval (register)'%x' % (solution)print (solution)else :raise Exception('Could not find the solution' )
04_angr_symbolic_stack
程序名字是符号化栈,对于这个题目我尝试了一下使用之前的02_angr_find_condition来进行约束输出求解,发现angr同样可以直接处理栈,岂不是直接一个输出条件的约束就可以吃遍逆向了?因为有些程序的分支结构十分大,angr会遍历所有可能的分支结构,简单的约束限制求解消耗的时间会十分巨大,所以我们需要进一步的学习来进行约束求解。
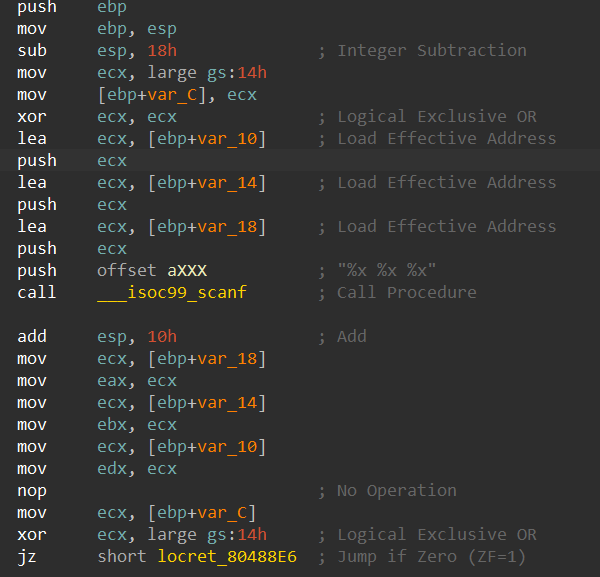
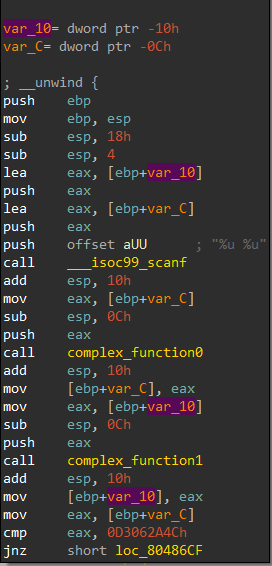
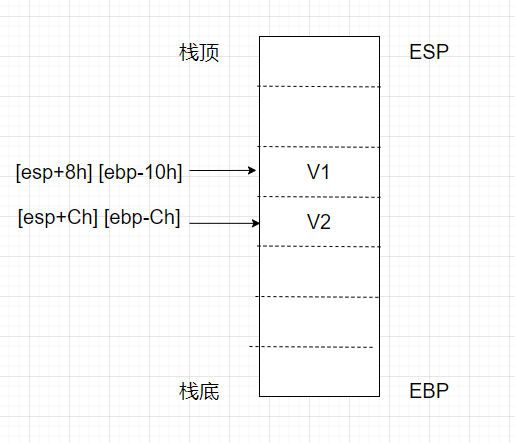
在程序里我们的输入是处于栈上的,在scanf过后执行了一个add esp, 10h的操作来清理scanf所产生的栈,因此我们真正的执行部分应该是在add esp, 10h之后,我们观察一下输入,可以看到v2最先被输入,然后便是v1,因此v2所在的栈空间是位于v1下方的 ( 栈向上增长 )。我们每次初始化栈时并不会有数据,而v1处于栈空间的中间,因此我们需要一个padding来帮我们覆写到对应v1所在的空间内。示意图如下:
v1距离栈顶还有0x8的空间,我们初始化栈时的padding将上面的0x8字节空间进行填充,之后的栈空间地址便是我们输入的v1地址。那么怎么进行初始化栈呢?栈开始时我们是将EBP和ESP两个栈指针的地址相等,然后入栈时栈顶指针ESP增加,我们在这个过程中是对栈进行了模拟操作,那么在angr中也有相应的模拟方式来实现模拟栈的初始化。
1 2 3 4 5 6 7 8 9 10 11 initial_state.regs.ebp = initial_state.regs.esp 'password0' , 32 ) 'password1' , 32 )0x8
那么我们便可以把这一连串代码加入到之前的第二题的代码之中,编写出如下脚本:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 from mimetypes import initimport sysimport angrimport claripydef main ():'./04_angr_symbolic_stack' 0x08048697 'password0' , 32 ) 'password1' , 32 )0x8 def is_successful (state ):return b'Good Job' in stdout_outputdef should_abort (state ):return b'Try again' in stdout_outputif simulation.found:0 ]eval (password0)eval (password1)'%u %u' % (solution0, solution1)print (solution)else :raise Exception('could not find the solution' )if __name__ == '__main__' :
在这个题目中我们学会了如何符号化栈空间,我们通过填充部分padding使我们的输入数据处于栈顶 ( 绕过了输入 ),同时与符号化寄存器相结合,让angr进行模拟,来代替输入的输入。
1 2 3 4 5 6 7 8 9 10 initial_state.regs.ebp = initial_state.regs.esp 'password0' , 32 ) 'password1' , 32 )
05_angr_symbolic_memory
看到题目便是我们要学习的符号化内存空间,观察一下输入的数据所在的位置,可以看到其处于在bss段上,属于一个内存区域内,我们所需要做的便是符号化内存空间。
与符号化栈空间有一点类似,我们需要设置 4 个符号向量来进行模拟输入,然后想办法将其放在内存空间里,angr提供有对应把符号项量放在内存中的函数,我们可以直接通过调用来对内存空间进行符号化。但在这之前我们需要找到bss段每个输入数据所在的地址值,将对应的地址传入到栈空间里。
1 2
其余部分和前面一个题的符号化栈空间是十分相像的,需要我们对输入进行符号化处理,然后将其地址和参数名传入到内存段即可。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 import angrimport sysimport claripyfrom Crypto.Util.number import long_to_bytesdef main ():'../program/05_angr_symbolic_memory' 0x08048601 'password0' , 64 ) 'password1' , 64 )'password2' , 64 )'password3' , 64 )0x09FD92A0 0x09FD92A8 0x09FD92B0 0x09FD92B8 def is_successful (state ):return b'Good Job.' in stdout_outputdef should_abort (state ):return b'Try again.' in stdout_outputif simulation.found:0 ]eval (password0)eval (password1)eval (password2)eval (password3)b' ' +long_to_bytes(solution1)+b' ' +long_to_bytes(solution2)+b' ' +long_to_bytes(solution3)print (solution.decode())else :raise Exception('Could not find solution' )if __name__ == '__main__' :
不过需要注意的是符号化向量对应的大小应该是对应的bit数据大小,而不是看其字节长度。在这个过程中我们将内存进行了符号化处理,然后将我们的符号化向量传入到bss段中去。
1 2 3 password = claripy.BVS('password' , <bit数据大小>)
06_angr_symbolic_dynamic_memory
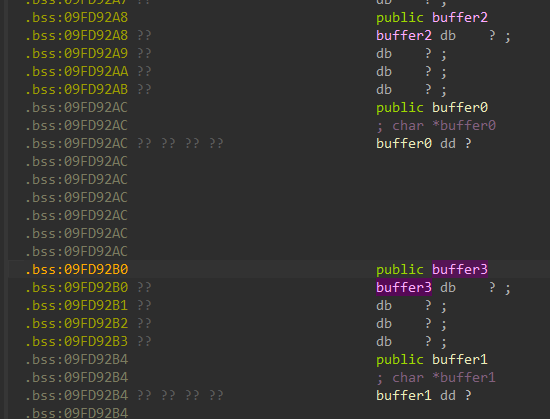
在这个题目中与上一个题目不同的是题目动态分配了两个指针变量,将我们的输入保存在堆空间上,使得我们需要将堆上的空间进行符号化处理,也就是malloc分配的空间是动态的但是其返回的变量buufer位于bss段,是静态的,那么我们可以伪造指针,使其指向的是一片可写内存,进而符号化处理。
我们可以看到空间内的定义数据都是处于bss段上的,我们便对其想办法来符号化。
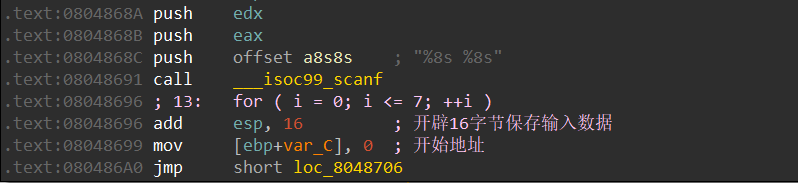
相当于我们模拟malloc分配地址空间,在bss段里找到一块空的空间来保存我们的输入数据。与此同时我们观察程序入口点可以看到程序在输入后有add esp, 16对scanf的栈空间进行整理,所以我们程序开始的地址为下面一行的0x08048699
接下来我们开始模拟malloc分配地址,并将其保存的输入符号化:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 'password0' , 64 ) 'password1' , 64 )0x09FD9160 0x09FD9180 0x09FD92AC 0x09FD92B4
我们整理一下脚本将符号化动态的内存空间加入到我们的第二题的代码组合便是我们的脚本:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 from operator import is_import sysimport angrimport claripyfrom Crypto.Util.number import long_to_bytesdef main ():'../program/06_angr_symbolic_dynamic_memory' 0x08048699 'password0' , 64 )'password1' , 64 )0x09FD9160 0x09FD9180 0x09FD92AC 0x09FD92B4 def is_successful (state ):return b'Good Job.' in stdout_outputdef should_abort (state ):return b'Try again.' in stdout_outputif simulation.found:0 ]eval (password0)eval (password1)b' ' + long_to_bytes(solution1)print (solution)print (solution.decode())else :raise Exception('Could not find solution' )if __name__ == '__main__' :
通过这个题目,我们了解到如何将动态的内存分配的地址进行转换为符号化,我们需要在bss段上找到对应大小的空间来保存我们的输入,然后将符号化后的输入导入到伪装的bss段地址处,之后便可以利用之前符号化内存的方式实现解题,我们学到的关键函数为:
1 2 3 4 5 6 7 8 9 10 11 12
参数:endness=project.arch.memory_endnessangr使用大端格式往内存中写入整数,这个参数告诉angr使用小端格式写入,这是x86的格式
07_angr_symbolic_file
看到题目发现里面是一个文件操作,从文件里进行读取数据,而我们需要将文件进行符号化处理,而angr也提供了对应的封装模块来供我们进行调用处理。下面列出其符号化文件的方式:
1 2 3 4 5 6 7 8 9 10 11 12 'XXX' 64 'password' , symbolic_file_size_bytes * 8 )
那么我们就可以直接在第二题的条件约束上扩展,加入这一串对文件进行格式化的操作指令:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 import sysimport angrimport claripyfrom Crypto.Util.number import long_to_bytesdef main ():'../program/07_angr_symbolic_file' 0x080488EA 'MRXJKZYR.txt' 64 'password' , symbolic_file_size_bytes * 8 ) def is_successful (state ):return b'Good Job.' in stdout_outputdef should_abort (state ):return b'Try again.' in stdout_outputif simulation.found:0 ]eval (password))print (solution.decode())else :raise Exception('Could not find solution' )if __name__ == '__main__' :
在这节里面我们学会了如何对文件进行符号化,来创建我们的约束求解器,其关键的函数如下:
1 2 3 4
08_angr_constraints
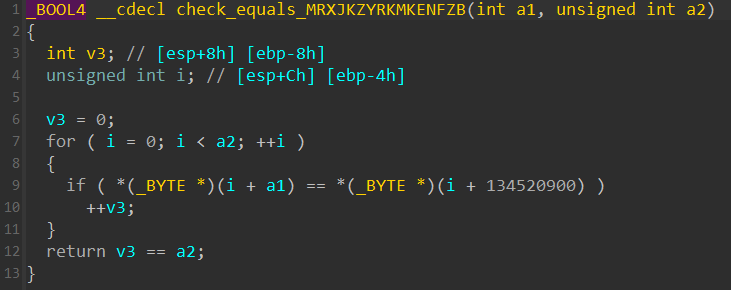
把程序拖入进IDA进行分析可以得到如下伪代码,可以看出程序将我们对输入在经过加密后与字符串MRXJKZYRKMKENFZB进行比较值,我们可以轻松的看出目的的比较,但是angr是遍历各个分支来进行模拟的,因此时间开销十分大,我们需要将其进行减小模拟的过程分支来缩短模拟的时间。
那么需要怎么操作?我们可以将buffer进行符号化处理,然后让程序来替代我们加密,之后我们切换到angr中,由我们来对加密后的数据进行检验,看是否与目的字符串相等。
1 2 3 4 0x08048669
此时我们需要转移到判断加密后的数据上:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 if simulation.found:0 ]0x0804A050 16 'MRXJKZYRKMKENFZB' eval (password))print (solution.decode())else :raise Exception('Could not find the sokution' )
那么脚本如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 import sysimport angrimport claripyfrom Crypto.Util.number import long_to_bytesdef main ():'../program/08_angr_constraints' 0x08048625 'password' , 16 *8 )0x0804A050 0x08048669 if simulation.found:0 ]0x0804A050 16 'MRXJKZYRKMKENFZB' eval (password))print (solution.decode())else :raise Exception('Could not find the sokution' )if __name__ == '__main__' :
在这一个题目中我们学会了将angr的遍历范围进行约束,来提升求解速度。
1 2 3 4 5
09_angr_hooks
拖入IDA分析,可以看到程序是由两个输入组成,当第一个输入错误时便会退出,其中第一次的输入经过加密后需要等于password,第二次的输入需要等于加密后的password
我们观察一下程序中需要hook的函数,可以看到程序执行的是进行比较字符串的操作,返回的是一个bool类型的数据,对此我们可以直接自己创建一个函数来进行直接比较并返回对应bool值,而不需要通过程序一个个的遍历判断,下面展示如何实现一个hook:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 0x080486A9 0x080486BB - 0x080486A9 @project.hook(check_equals_caller_addr, instruction_to_skip_length ) def skip_check_equals (state ):0x0804A054 16 'MRXJKZYRKMKENFZB' 1 , 32 ), 0 , 32 )
那么程序的关键部分也便实现了,我们可以编写如下脚本:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 import sysimport angrimport claripydef main ():'./09_angr_hooks' 0x080486A9 0x080486BB - 0x080486A9 @project.hook(check_equals_caller_addr, length = instruction_to_skip_length ) def skip_check_equals (state ):0x0804A054 16 'MRXJKZYRKMKENFZB' 1 , 32 ), 0 , 32 ) def is_successful (state ):return b'Good Job.' in stdout_outputdef should_abort (state ):return b'Try again.' in stdout_outputif simulation.found:0 ]print (solution.decode())else :raise Exception('Could not find the solution' )if __name__ == '__main__' :
通过这个例子我们学会了使用hook来代替程序中的函数,并执行我们自己构造的函数。其关键函数如下
1 2 3 4 5 6 7 8 9 10 @project.hook(check_equals_caller_addr, length = instruction_to_skip_length ) 1 , 32 ), 0 , 32 )
10_angr_simprocedures
上一道题目我们是只利用一个hook进行模拟了一个函数,但是在这个题目里面我们可以找到许许多多的函数,如果一个个写会累死的 ( bushi )
所以在这个题目中我们需要想办法hook一片的函数,那么我们为什么不想一下我们把名字hook了,意味着每次调用这个相同名字的函数时执行的便是我们自己编写的过程。实现如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 class mySimPro (angr.SimProcedure ):def run (self, user_input_addr, user_input_length ):'MRXJKZYRKMKENFZB' return claripy.If(1 ,32 ), 0 ,32 )'check_equals_MRXJKZYRKMKENFZB'
那么脚本编写如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 from pydoc import describeimport angrimport sysimport claripydef main ():'./09_angr_hooks' class mySimPro (angr.SimProcedure ):def run (self, user_input_addr, user_input_length ):'MRXJKZYRKMKENFZB' return claripy.If(1 ,32 ), 0 ,32 )'check_equals_MRXJKZYRKMKENFZB' def is_successful (state ):return b'Good Job.' in stdout_outputdef should_abort (state ):return b'Try again.' in stdout_outputif simulation.found:0 ]print (solution.decode())else :raise Exception('Could not find the solution' )if __name__ == '__main__' :
在这道题目中我们学习了如何hook一个函数名,从而使程序在每次运行到这个函数名时执行的都是我们hook后的函数,对此我们利用继承的方式对其进行hook:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 class ReplacementCheckEquals (angr.SimProcedure ):def run (self, to_check, length ):return claripy.If(1 , 32 ), 0 , 32 )'check_equals_MRXJKZYRKMKENFZB'
11_angr_sim_scanf
随着angr的更新迭代,似乎逐渐支持了scanf这一类的函数,可以不需要手动模拟scanf,angr可以直接自动化模拟,问了一下草莓师傅,似乎angr现在还能自动hook,关于这个我也没有去测试过,也不是太了解这些。
根据题目要求,需要我们模拟scanf来进行模拟输入,实现方式似乎类似于hook函数名,同样需要我们进行继承angr下的SimpProcedure,只是里面的一些函数发生了变化:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 class ReplacementScanf (angr.SimProcedure ):def run (self, fmt, scanf0_addr, scanf1_addr ):'scanf0' , 4 *8 ) 'scanf1' , 4 *8 )globals ['solution0' ] = scanf0 globals ['solution1' ] = scanf1'__isoc99_scanf'
通过上述模拟可以将输入的字符串保存到内存空间,那么我们便可以写出如下代码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 import sysimport angrimport claripydef main ():'../program/11_angr_sim_scanf' class ReplacementScanf (angr.SimProcedure ):def run (self, fmt, scanf0_addr, scanf1_addr ):'scanf0' , 4 *8 )'scanf1' , 4 *8 )globals ['solution0' ] = scanf0 globals ['solution1' ] = scanf1'__isoc99_scanf' def is_successful (state ):return b'Good Job.' in stdout_outputdef should_abort (state ):return b'Try again.' in stdout_outputif simulation.found:0 ]globals ['solution0' ] globals ['solution1' ]'%u %u' % (solution_state.se.eval (solution0), solution_state.se.eval (solution1))print (solution)else :raise Exception('Could not find the solution' )if __name__ == '__main__' :
我们在这个题中同样利用到了符号化函数名的方式来对一堆的scanf进行模拟,并将其保存在内存段里,具体函数如下:
1 2 self.state.globals ['solution0' ] = scanf0 globals ['solution0' ]
12_angr_veritesting
在这个题目中与01的avoid来约束目标输出字符串,但是这个题目中循环的次数较大,如果直接套用01的脚本可能会出现路径爆炸 ( angr模拟执行时遍历的路径是成指数级上涨,如果都需要需要执行那么便会引发错误 ),我们之前所做的hook函数,添加约束条件都是有效的防止路径爆炸的操作,我们接下来采用一个新的方式来解决路径爆炸的问题:
1 sm=p.factory.simulation_manager(istate,veritesting=True )
这个函数让我们直接忽视循环结构,直接进行求解,一般耗时会比较长。
加入这个防止路径爆炸的脚本为:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 import sysimport angrdef main ():'../program/12_angr_veritesting' True ) def is_successful (state ):return b'Good Job.' in stdout_outputdef should_abort (state ):return b'Try again.' in stdout_outputif simulation.found:0 ]print (solution)else :raise Exception('Could not find the solution' )if __name__ == '__main__' :
13_angr_static_binary
这个示例的逻辑和01题是一样的,主要不同的地方是在于这个程序是静态链接编译的,所以程序中包含了一些libc的函数实现,但是这里可能会存在两个问题:
这些函数里面隐藏一些出题人的坑;
这些函数里面的实现可能会依赖其他的系统函数或者实现方式不相同.所以12 题主要是让我们通过Hook 的方式重定向函数中被调用的libc 的函数
首先,Linux 下启动main() 函数需要通过__libc_start_main 对程序进行初始化,然后再跳转到main() 函数;其次,在main() 函数里面调用了printf ,scanf ,puts ,所以我们需要通过Hook 来重定向它们.
幸运的是,我们不需要重新实现这些函数的实现,Angr 代码库里面已经帮我们实现了一部分libc 的函数库,所以我们只需要倒入它们即可.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 import angrimport sys1 ])True ) 0x804ed40 , angr.SIM_PROCEDURES['libc' ]['printf' ]()) 0x804ed80 , angr.SIM_PROCEDURES['libc' ]['scanf' ]())0x804f350 , angr.SIM_PROCEDURES['libc' ]['puts' ]())0x8048d10 , angr.SIM_PROCEDURES['glibc' ]['__libc_start_main' ]())def is_successful (state ):return 'Good Job.' in str (stdout_output) def should_abort (state ):return 'Try again.' in str (stdout_output) if simulation.found :0 ]print (solution_state.posix.dumps(sys.stdin.fileno()))
通过上述题目,我们了解到了如何将静态链接中的库函数进行hook,从而来获取libc 的函数库:
1 2 project.hook(<调用地址>, angr.SIM_PROCEDURES ['<系统库名>' ]['<系统函数名>' ]()) # hook库函数SIM_PROCEDURES [ 系统库名 ] [ 系统函数名 ] () => 获取Angr 内部实现的系统函数
14_angr_shared_library
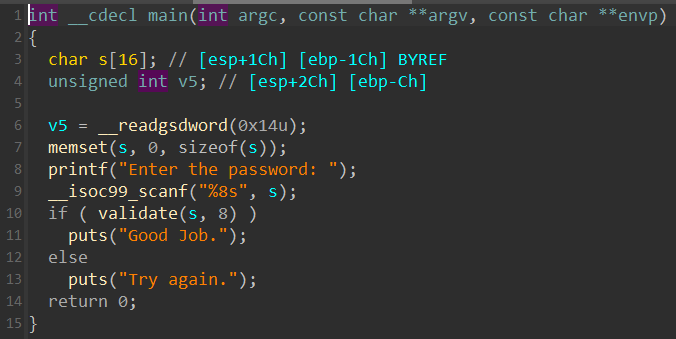
在编译好的程序中我们可以看到有一个validate函数对我们的输入进行了比较,但是进入这个函数却发现没有相关的实现方式
这是因为validate在共享库里,即程序提供的so中,事实上so也算是一种可执行文件,但是没有经过符号链接,我们需要的便是通过angr加载共享库,然后伪造参数来对validate函数进行调用。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 def main (argv ):1 ] 0x400000 'main_opts' : {'custom_base_addr' : base0x3000000 , 32 ) 0x6D7 8 , 32 )) 'password' , 8 * 8 ) 0x783 ) if simulation.found:0 ]0 ) eval (password)print (solution)
15_angr_arbitrary_read
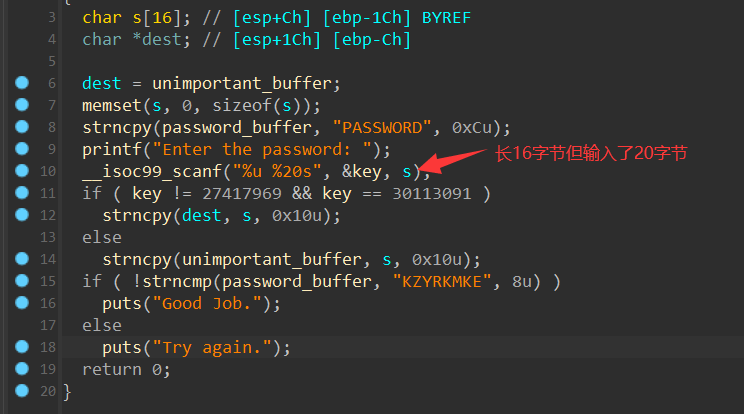
单纯的从程序上看的话似乎程序一直是输入错误,但是我们到栈上看输入的变量,可以发现读入了20个字符,但是栈空间中到s的距离仅有16,所以意味着多出来的4字节会覆盖s保存的地址,因此我们可以直接用这4字节进行替换到输出正确的地址处。
所以脚本可以如下进行编写:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 def main (argv ):1 ]class ReplacementScanf (angr.SimProcedure ):def run (self, format_string, check_key_address,input_buffer_address ):'scanf0' , 4 * 8 ) 'scanf1' , 20 * 8 ) for char in scanf1.chop(bits=8 ):'0' , char <= 'z' ) globals ['solution0' ] = scanf0 globals ['solution1' ] = scanf1'__isoc99_scanf' def check_puts (state ):4 , 4 , endness=project.arch.memory_endness) if state.se.symbolic(puts_parameter): 0x4D525854B if copied_state.satisfiable(): return True else :return False else :return False def is_successful (state ):0x8048370 if state.addr == puts_address:return check_puts(state)else :return False if simulation.found:0 ]eval (solution_state.globals ['solution0' ])eval (solution_state.globals ['solution1' ],cast_to=bytes ) print (solution0,solution1)
通过这个题目我们可以学习到添加对输入的约束,和复制状态的上下文,以及序列化内容转化为字符串:
1 2 3 4 5 state.copy() eval (求解变量,cast_to=bytes )
16_angr_arbitrary_write
从程序看,其最终目的是将password_buffer里面的字符替换成KZYRKMKE,但是程序中彬没有指向password_buffer的变量,同时我们也发现与上一个题目一样函数存在溢出的漏洞,所以我们利用这个4字节溢出将目的password_buffer的值修改,达到输出正确的目的。
脚本如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 def main (argv ):1 ]class ReplacementScanf (angr.SimProcedure ):def run (self, format_string, check_key ,input_buffer ):'scanf0' , 4 * 8 )'scanf1' , 20 * 8 )for char in scanf1.chop(bits=8 ):'0' , char <= 'z' )globals ['solution0' ] = scanf0globals ['solution1' ] = scanf1'__isoc99_scanf' def check_strncpy (state ):4 , 4 , endness=project.arch.memory_endness) 8 , 4 , endness=project.arch.memory_endness)12 , 4 , endness=project.arch.memory_endness)if state.se.symbolic(strncpy_dest) and state.se.symbolic(src_contents) : if state.satisfiable(extra_constraints=(src_contents[ -1 : -64 ] == 'KZYRKMKE' ,strncpy_dest == 0x4D52584C )): 1 : -64 ] == 'KZYRKMKE' ,strncpy_dest == 0x4D52584C )return True else :return False else :return False def is_successful (state ):0x8048410 if state.addr == strncpy_address:return check_strncpy(state)else :return False if simulation.found:0 ]eval (solution_state.globals ['solution0' ])eval (solution_state.globals ['solution1' ],cast_to=bytes )print (solution0,solution1)
17_angr_arbitrary_iump
一打开程序一看就只有一个输入,和一个输入错误,我们查看其函数,发现在某个地址处可以发现有输出Good,我们可以判断出这个是将ret的返回地址进行覆盖然后跳转到对应的输入正确函数地址处。
脚本如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 def main (argv ):1 ]True ,'active' : [initial_state],'unconstrained' : [],'found' : [],'not_needed' : []class ReplacementScanf (angr.SimProcedure ):def run (self, format_string, input_buffer_address ):'input_buffer' , 64 * 8 ) for char in input_buffer.chop(bits=8 ):'0' , char <= 'z' )globals ['solution' ] = input_buffer'__isoc99_scanf' while (simulation.active or simulation.unconstrained) and (not simulation.found): for unconstrained_state in simulation.unconstrained:def should_move (s ):return s is unconstrained_state'unconstrained' , 'found' , filter_func=should_move) if simulation.found:0 ]0x4D525849 ) eval (solution_state.globals ['solution' ],cast_to = bytes ) print (solution)